Tailscale - a very clever (and free) VPN.
I don't trust public WiFi connections, and I think I'm right to be cautious; there are many risks in connecting to an 'open' network. My mate Ed reminded me about Tailscale and I finally got around to trying it. What an absolute revelation...
I don't trust public WiFi connections, and I think I'm right to be cautious; there are many risks in connecting to an 'open' network. It's fair to say that SSL and HTTPS have (in frighteningly recent times, really) brought a degree of security to web traffic, but it's easy to be complacent when going into a fast food restaurant, shopping centre or pub (especially when the mobile phone signal is poor!)
The benefits of a VPN are myriad - I'm sure you've seen plenty of those adverts that tell of 'malware-free downloads' and 'untrackable links' - what I'm more interested in is being able to connect to my home network (to get something from the shared home file server or just check to see if I left the printer on) and to take control of how my web browsing and conversations get out to the internet.
Until recently I ran a very simple IPSEC VPN on my Raspberry Pi to which I could connect with my mobile or Windows device (with a bit of fiddling about) but it started being a little unreliable, and often wouldn't connect from my Android device (I blame software security upgrades!)
My mate Ed reminded me about Tailscale and I finally got around to trying it. What an absolute revelation - not only does it do a point-to-point VPN, but it can open up a route to a private network (so I can run it on my Raspberry Pi at home) and act an exit node to the internet (for which I can use my Always Free Oracle VPC, since it's got a 1 Gb/s connection). All at no cost. Yup. Free.
Setting it up
It's really easy to set up - all that's required is to authenticate with a fairly mainstream service (Google, Microsoft, Apple etc) and then follow the instructions to install it on a server (to act as a router) or a client device (from its native app store). The main console shows all the devices that are in the 'tailnet' and with a bit of configuration, it's possible to add the LAN and internet exit nodes
Sharing the local network
On my Raspberry Pi, I followed the installation instructions and then followed the instructions to set up the subnet router node. Essentially, this is:
- enable IP forwarding:
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
sudo sysctl -p /etc/sysctl.d/99-tailscale.conf
- advertise the routes by restarting the tailscale service
sudo tailscale up --advertise-routes=192.168.0.0/24,192.168.1.0/24
- go to the admin console and enable the route:
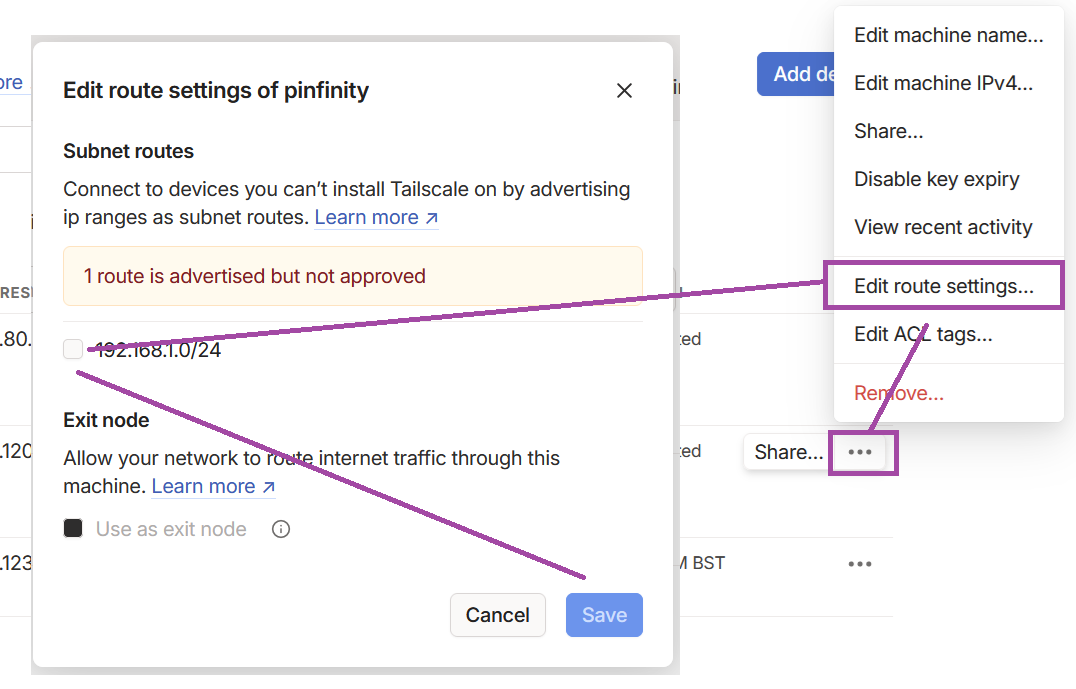
Whenever I connect my mobile device to Tailscale, I can then connect to any device on my home network as if I were at home.
Creating an exit node
An exit node (through which it's possible to connect to the internet) is created in a very similar way:
- enable IP forwarding:
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
echo 'net.ipv6.conf.all.forwarding = 1' | sudo tee -a /etc/sysctl.d/99-tailscale.conf
sudo sysctl -p /etc/sysctl.d/99-tailscale.conf
- restart the tailscale service as an exit node
sudo tailscale up --advertise-exit-node- go to the admin console and enable it:
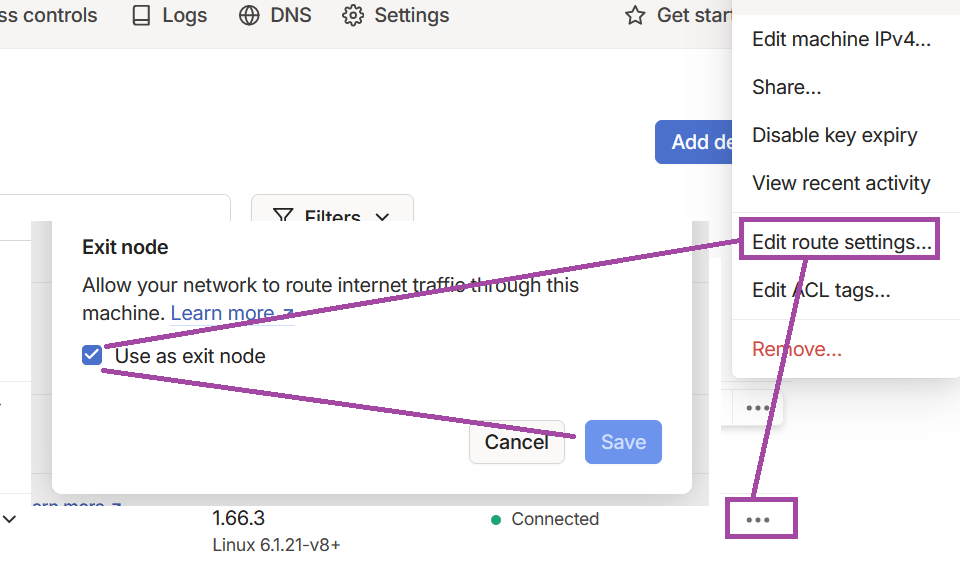
It's then possible to select this as an exit node from the Tailscale app:
